Plugin Information |
|---|
View Chatter Notifier on the plugin site for more information. |
Older versions of this plugin may not be safe to use. Please review the following warnings before using an older version:
Features
This is a plugin for Jenkins that will post build results or custom text during a build to a Chatter feed in Salesforce. You can configure it to post to a specific User (e.g. a build user), a specific group (e.g. a group that owns the build), or a specific record (perhaps you have a custom object that tracks build configs).
Minimum Requirements
This plugin requires at least version 1.22 of the Credentials Plugin.
Configure
- Install the Chatter Plugin using the Jenkins Plugin Manager and restart the server
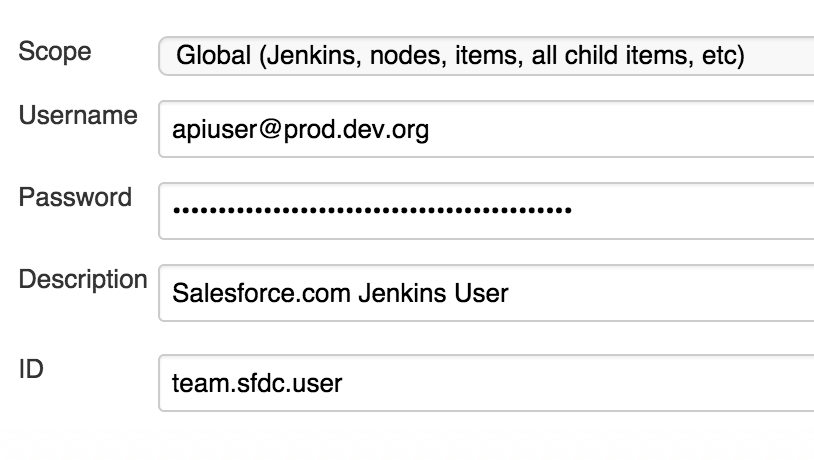
- Create new credentials of the kind "Username with Password"
- Remember to include your users API security token if needed as part of the password
- Remember to include your users API security token if needed as part of the password
- Create or update a Freestyle Job:
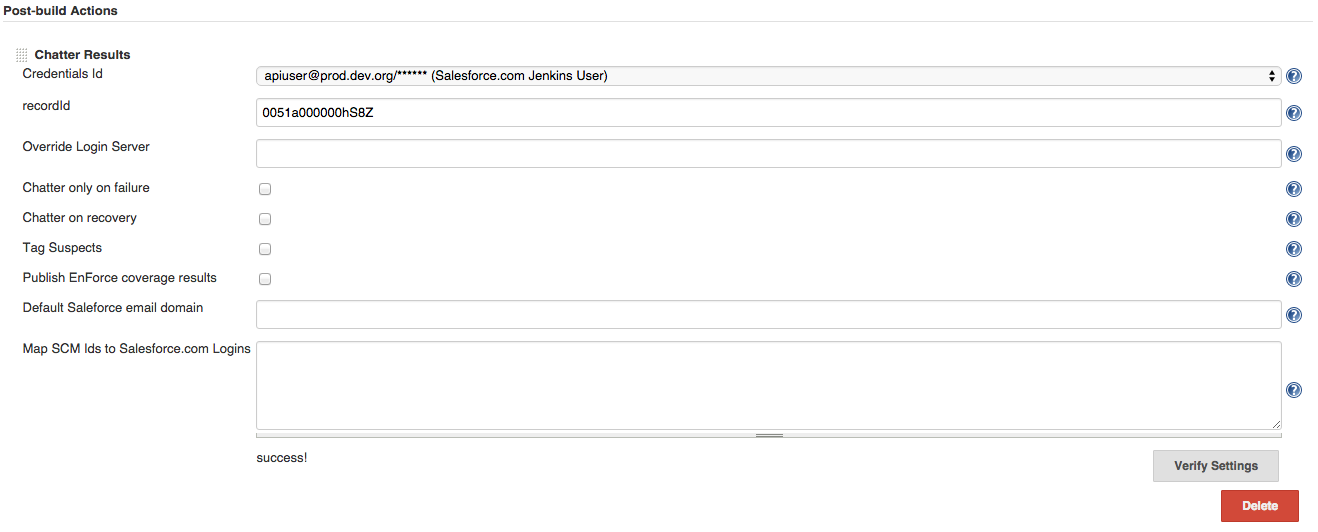
- Add post-build action -> Chatter Results or Add build step → Post to Chatter
- Populate the fields as needed (see the inline help for more details):
- Credentials
- Optional server URL to login to
- Record id (record, user, or group) to post results to (leave this blank to post to the user's wall)
- Add a step to a Pipeline Job:
- Configure a step within the context of a node:
- Example:
chatterPost body: "This is a Chatter post from a pipeline! ${env.JOB_NAME} ${env.BUILD_DISPLAY_NAME}", credentialsId: 'JENKINS_CREDENTIAL_ID', recordId: 'SOME_RECORD_ID'
- Example:
- See the README in GitHub or the Jenkins Snippet Generator for more information.
- Configure a step within the context of a node:
Changelog
v2.1.0
- Add a build step which can also be used as a pipeline step to post custom text to Chatter.
v2.0.5
- Security release to address a potential issue where any user with Jenkins.READ to invoke the method against a custom credentials-capturing server. It allowed leaking credentials if they were not scoped properly. It also allowed any attacker with Jenkins.READ to easily get a list of credential IDs vulnerable to the attack.
v2.0.4
- Utilize proxy configuration (authenticated and unauthenticated from Manage Jenkins → Manage Plugins → Advanced (No Proxy Hosts remains unimplemented)
v2.0.3
Give contextual build status (FIXED, STILL FAILING)
v2.0.2
- Hosted on jenkins-ci.org
- Now requires at least version 1.22 of the Credentials Plugin