In order to use SSL with TestLink Plugin you have to import the certificate of your TestLink server to the list of trusted certificates of your JRE. If you try to use the plug-in without importing your certificate you may see an error similar to the one in the following screen.
First you have to obtain a local copy of your certificate. You can do it with FIrefox, for instance. Just open your https URL, right click on the displayed page, Show Info / Security, look for the export button and save it to somewhere in your computer.
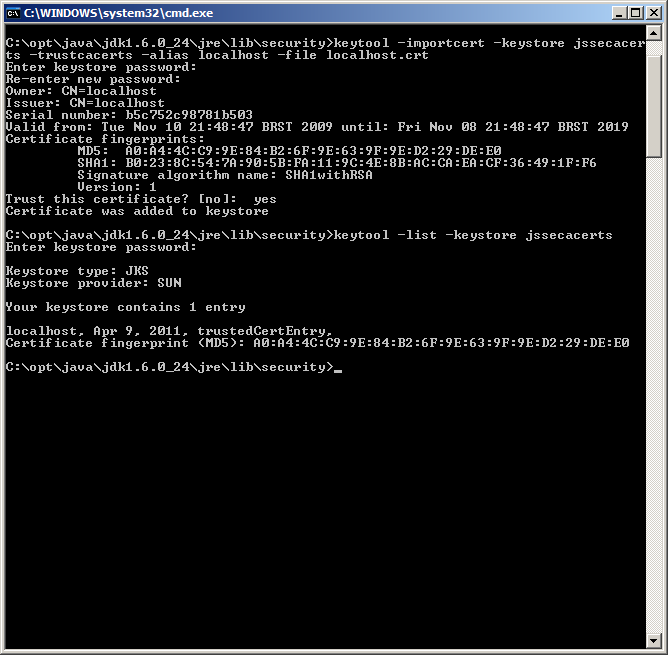
Now you need to import this certificate into a keystore.
keytool -importcert -keystore jssecacerts -trustcacerts -alias localhost -file localhost.crt
My locale was set to Brazil and language to Brazilian Portuguese and for some reason after importing the certificate I faced issues when trying to list it. Then I changed by region settings to United States and American English, imported the certificate again and it worked. Tricky no?
Now you have to tell the JRE that it has a new place to look for certificates (your generated keystore). Open %JENKINS_HOME%/jenkins.xml and look for the arguments tag (<arguments>). Add the following properties into it.
-Djavax.net.ssl.keyStoreType=jks -Djavax.net.ssl.keyStore=C:\opt\java\jdk1.6.0_24\jre\lib\security\jssecacerts -Djavax.net.ssl.keyStorePassword=kinoshita -Djavax.net.ssl.trustStore=C:\opt\java\jdk1.6.0_24\jre\lib\security\jssecacerts -Djavax.net.ssl.trustStorePassword=kinoshita
It will look like follows after you are done.
Now just start jenkins and execute your build and start using the plug-in with SSL.
Depending on your environment settings these instructions may vary a little. But the basic idea is add your server certificate into the list of trusted certificates of your JRE. Hope it helps :-).
There is another way to use the plug-in with SSL, it would require a small modification in the code that would accept any SSL connection, not minding about certificates, as pointed in http://ws.apache.org/xmlrpc/ssl.html. However it would be a risky in productive environments.